Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API
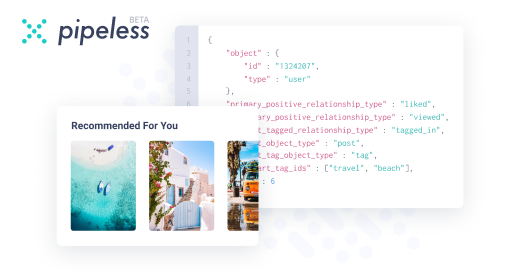
From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Related Rants

 Clearly right now... Just spent 2 days writing a minesweeper clone because I wanted the ability to undo.
It's...
Clearly right now... Just spent 2 days writing a minesweeper clone because I wanted the ability to undo.
It's...
When I made a PoC xss thingy.
So this webapp (which I was locally hosting) had a message functionality that allowed iframes to be sent through, but they could only originate from a specific domain. They used a bad regex tho, as the workaround was on an OWASP wiki page, which was the third search result for 'XSS'. I then used this iframe to load in a different page on this app where I could inject js in the title field. Then I discovered this field has a length limit, but I could just fit in a script that would base64 decode the hash part of the URL and eval it. I then updated the iframe to include a script that would automatically change the message signature of anyone who loaded it to include the iframe again in their message signature. Because these two pages were from the same domain, I had gained full control of the messaging app too, allowing me to do this and circumvent the csrf system.
I felt like I had achieved something.
rant
wk79
xss
iframes