Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API
From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
The connection isn't just SSID based. It can differentiate between two networks even if they have the same name.
You can however switch your network card to monitor mode(if it's compatible) and sniff packets. Most are encrypted though. -
 CCTrollz7447y@hellvetica I have tried to use Kali and the included tools like Airmon but unfortunately I am just using my built in wireless card so no monitor mode. Any suggestions for a good USB dongle supporting it?
CCTrollz7447y@hellvetica I have tried to use Kali and the included tools like Airmon but unfortunately I am just using my built in wireless card so no monitor mode. Any suggestions for a good USB dongle supporting it? -
@CCTrollz i think a simple edimax dongle should work, but don't take my word for it.
-
 afreitas2557yI love this site so much. 10 comments and no mention of morals/ethics. Thank you all
afreitas2557yI love this site so much. 10 comments and no mention of morals/ethics. Thank you all -
 CCTrollz7447y@afreitas its Grey Hat. Not strictly given permission but am also trying to prove a point.
CCTrollz7447y@afreitas its Grey Hat. Not strictly given permission but am also trying to prove a point. -
 sudoguy5947yWhat credentials do you want to capture? If you want to capture password of the legit AP then you can't do it, because the plain password is not transmited (search for wpa handshake for exact mechanism). Your only chance is capturing handshake (airodump-ng) with the legit AP and than launching dictionary/brute force on sniffed traffic to guess the password (aircrack-ng).
sudoguy5947yWhat credentials do you want to capture? If you want to capture password of the legit AP then you can't do it, because the plain password is not transmited (search for wpa handshake for exact mechanism). Your only chance is capturing handshake (airodump-ng) with the legit AP and than launching dictionary/brute force on sniffed traffic to guess the password (aircrack-ng).
If you want to capture credentials for websites etc. then most of it will be encrypted. You can try make phishing site (SE toolkit) and spoof DNS, but that won't work on sites using HSTS, HPKP and alerts the users. So there is no easy way to start harvesting the credentials.
Related Rants

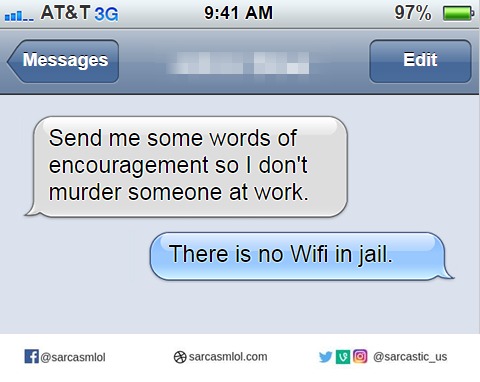 And that was enough encouragement
And that was enough encouragement correctly named devices
correctly named devices When you "fix" a bug not by actually fixing the bug but by disabling the user's ability to cause the bug.
When you "fix" a bug not by actually fixing the bug but by disabling the user's ability to cause the bug.
So I found a thing. On my laptop, I am able to create a hotspot. So someone can connect to it and I can share my internet access. Couldn't I theoretically impersonate a wifi name, by setting up the hotspot to use the SSID of the target network, then the clients that already have access to the target network would feed me the network credentials? If so, how would I go about capturing the creds?
undefined
sneaky-beaky like
hackerman
wifi